Favorite Intruder is a cloud-based vulnerability scanner that helps to find weaknesses in your online systems before the hackers do. It saves you time by proactively scanning for new threats as well as offering a unique threat interpretation system that makes vulnerability management easy. Find your weaknesses,before the hackers do. Intruder is an online vulnerability scanner that finds cyber security weaknesses in your digital infrastructure, to avoid costly data breaches. Vulnerability scanning is the only automatic way to protect your website or web application from malicious hacker attacks. In addition, you should do manual penetration testing after a vulnerability scan. You should use web application firewalls only as temporary protection before you can fix vulnerabilities.
- Vulnerability Scanner Software
- Vulnerability Scanner Online
- Vulnerability Scanner Pc
- Vulnerability Scanner Tools
- Vulnerability Scanner Definition
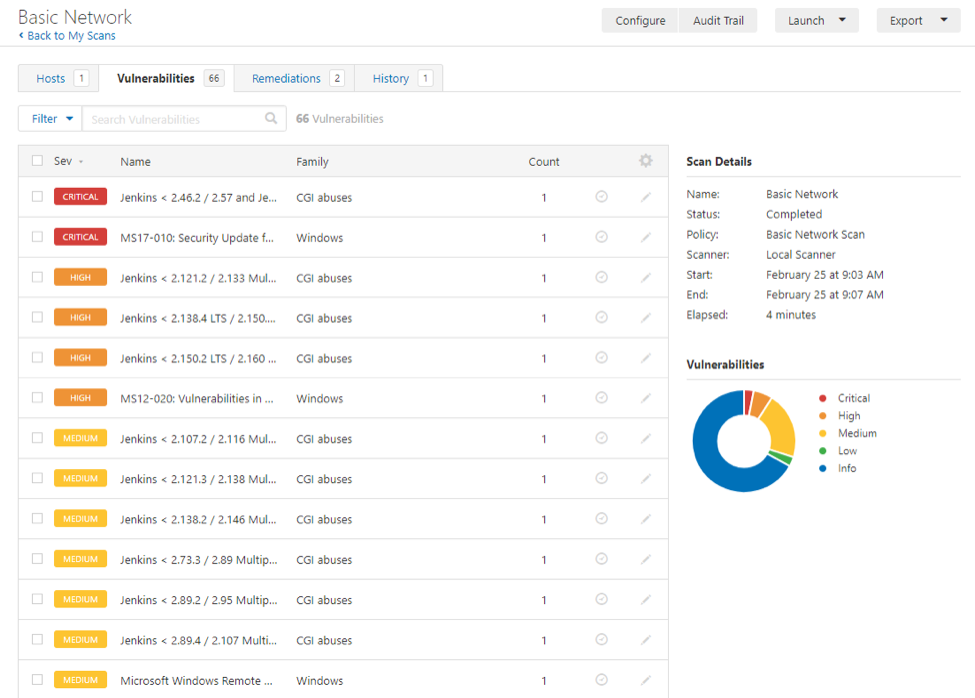
A vulnerability scanner is a tool employed by security teams to inspect their endpoints for vulnerabilities and various loopholes. ManageEngine Vulnerability Manager Plus is comprehensive vulnerability management software for SMBs and enterprises that enables organizations to not only detect vulnerabilities and misconfigurations continuously but also gain insights into risks so as to prioritize their response. Organizations can utilize the built-in remediation capabilities to complete the vulnerability management workflow from a unified console.
Below we cover:
What are the limitations of traditional vulnerability scanners?
Traditional vulnerability scanners:
- Offer only a point-in-time snapshot of your network and lack continual visibility. However, a new vulnerability springs up every 90 minutes. Not only that, systems and configurations change all the time, and a new device or software instance enters your network every now and then. Every new opportunity or change opens up new avenues for risk.
- Are too narrowly focused and require multiple siloed tools to scan other attack vectors beyond software vulnerabilities. This results in redundant scans, straining network load and bandwidth consumption.
- Neither present the gathered scan data in a consolidated, easy-to-understand dashboard nor offer contextual information to understand risk and triage response.
- Require integration with additional remediation tools to mitigate the issues identified, resulting in a siloed, inefficient workflow that makes the process of remediating risk slow and complex.
Vulnerability scanning and beyond from one unified platform
Vulnerability scanning alone amounts to nothing if the risks posed by vulnerabilities are not mitigated in a timely fashion. To achieve this with ease, Vulnerability Manager Plus integrates vulnerability scanning and assessment, patch management, and security configuration management, providing unified visibility, tracking, and better control from detection to closure—all from a central location.
Now you can achieve end-to-end vulnerability management with just one console and one agent, which makes Vulnerability Manager Plus easily scalable to dynamic environments. This also eliminates the need for redundant scans, as a single scan will fetch all the vulnerabilities, configuration errors, and patch information and automatically correlate this data, helping to accomplish direct, swift remediation.
Comprehensive vulnerability scanning
Eliminating blind spots is the basis of successful vulnerability management. To achieve this, Vulnerability Manager Plus:
- Detects known or emerging vulnerabilities across all your network endpoints, including workstations, laptops, servers, web servers, databases, virtual machines, and content management systems.
- Offers continuous visibility into your endpoints, whether they are located at the local office, in a demilitarized zone, at a remote location, or always on the move.
- Extends your visibility beyond just vulnerabilities and identifies misconfigurations, high-risk software, active ports, and much more.
Intuitive dashboards with rich contextual information
Frustrated with a deluge of scan data? The Vulnerability Manager Plus web console features a score of easy-to-understand, interactive dashboards that not only offer a bird's-eye view of your organization's overall security posture but also bring you clarity into which areas matter most.
- Vulnerability dashboard
- Security configurations management dashboard
- Patch dashboard
- Systems dashboard
- Drilled-down system view
Risk-based vulnerability assessment
Visualize, analyze, and prioritize your response to exploitable and impactful vulnerabilities based on:
- CVSS scores and severity ratings.
- The availability of exploits.
- A security news feed that's continually updated with articles on vulnerabilities that attackers are discussing, experimenting with, or using, and current exploits circulating in the wild.
- Vulnerability age.
- Affected asset count.
- A drilled-down view of assets that displays whether web servers, databases, or content management systems are installed on them, along with vulnerabilities on those installations.
- CVE impact type.
- Patch availability.
- A dedicated view to swiftly pinpoint zero-day or publicly disclosed vulnerabilities.
Learn more about the importance and benefits of risk-based vulnerability management over traditional vulnerability management.
Built-in remediation
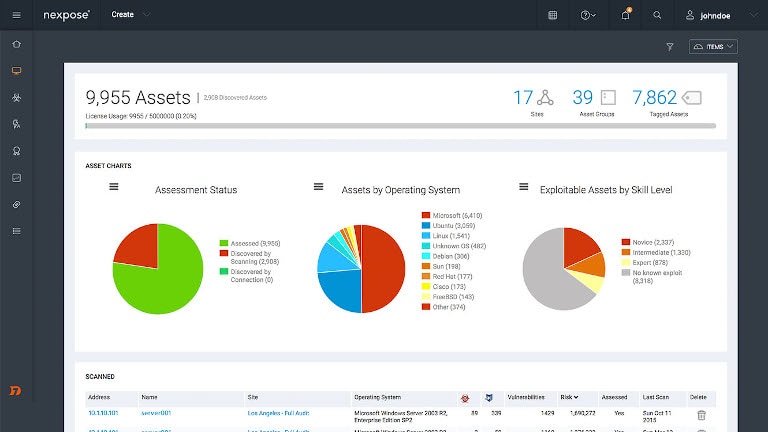
The built-in patching functionality automatically correlates patches with prioritized vulnerabilities, allowing you to remediate vulnerabilities in an instant without relying on a dedicated patching tool. You can also schedule an automated patch management task with flexible deployment policies to keep your systems up-to-date with the latest patches while you focus your attention on the vulnerabilities that matter. Furthermore, you can deploy corrective security configurations and remove high-risk software on all affected machines directly from the console.
Vulnerability Scanner Software
Vulnerability reporting
All your vulnerability management efforts are essentially futile if you can't evaluate your progress. Vulnerability Manager Plus offers a massive library of executive reports, granular report templates, and customizable query reports that you can use to scrutinize your network security, communicate risks, track progress, and report on security regulations to executives. These reports are available in different formats, including PDF, CSV, and XLSX. You can either generate reports on demand or schedule them to be sent directly to security executives, administrators, and enterprise risk management teams with just a click from the console.
Scan and secure your endpoints now with 30 days of free, unlimited access.
Get a personalized demoTry for freeHow does ManageEngine's vulnerability scanner work?
Below is a detailed breakdown of how Vulnerability Manager Plus works:
- Our team of vulnerability experts meticulously probe the internet through a myriad of sites to find all possible vulnerabilities and threats that have recently been disclosed, along with information on the patches required to mitigate them. These details are tested for accuracy, and the vulnerability information is mapped to their respective patches. This is the most integral function of any vulnerability scanner, so it is done with utmost accuracy.
- After thorough testing, the information regarding the vulnerabilities and their corresponding patches is hosted in the Central Vulnerability Database maintained by our security specialists. These vital details are periodically synchronized with the vulnerability database maintained in the Vulnerability Manager Plus server present in the user's enterprise. The sync interval can be scheduled by the IT admin according to their convenience.
- Agents are installed on all of the enterprise’s endpoints so the devices can be managed directly from the server console. However, enterprises today have multiple offices and their users are constantly on the go, further complicating a vulnerability scanner's tasks. As an all-inclusive vulnerability scanning tool, Vulnerability Manager Plus can tackle this efficiently. Endpoints in local or remote offices can be managed by configuring the SOM policy. Roaming users who are always on the move will be assigned a default remote office, which helps keep them managed.
- The agents will conduct a detailed vulnerability scan based on the new discovered vulnerability details from the servers, repeatedly checking all endpoints for the existence of those vulnerabilities. The scan results are displayed to the IT admin and automatically updated every time a scan occurs.
- Vulnerability Manager Plus' scope as a vulnerability scanner doesn't end here; valuable information such as the exploit status, severity, and patch availability is displayed to the IT admin along with the vulnerability details, based on which they can strategically prioritize which vulnerability requires immediate attention.
- Thanks to the Automated Patch Deployment feature, the patches for vulnerabilities can also be deployed automatically from the product console as and when they are discovered. This vulnerability scanner, unlike others, doesn't compromise end users’ productivity during patching, as it comes with the option to create flexible patch deployment policies. Vulnerability Manager Plus empowers the admin to squash any vulnerability in their network in just a few clicks.
Sadly, threats can still enter your enterprise through other loopholes. But fret not. ManageEngine's vulnerability scanner Vulnerability Manager Plus has got you covered from all sides. With extensive features to manage security and system misconfigurations, you can keep all kinds of threats at bay.

Frequently asked questions about vulnerability scanning
What are vulnerabilities?
Vulnerabilities are security loopholes present in any software. If exploited, these flaws can allow attackers to gain unauthorized access to sensitive information or generally cause havoc, putting entire organizations at risk. External security researchers and concerned vendors are constantly scrutinizing publicly available software to identify vulnerabilities. Any discovered vulnerability is registered with a CVE ID and assigned a CVSS score based on the damage its exploit might cost. The vendor is then given a deadline to come up with a patch to remediate the vulnerability before it is exposed to the public. Once a vulnerability is disclosed publicly, anyone can try to exploit it.
This is not the end; there are some players who might not abide by the above rules at all. If a vulnerability is identified by them, they might disclose it without giving the vendor any warning, or worse, they might just proceed to find an exploit. In any of these cases, if your organization uses software with a disclosed vulnerability, you will be at risk.
Why do you need a vulnerability scanner?
Vulnerability Scanner Online

Even if patches exist for vulnerabilities, most organizations still fall prey because of their lack of awareness about them. If exploited, vulnerabilities can further proliferate into large-scale security breaches that might lead to financial losses or major data leaks in the affected organizations.
The most important part of establishing a secure environment is to always be informed of vulnerabilities, after which you can decide how to mitigate them. With a proper vulnerability scanner installed in your enterprise, you can expediently discover and remediate these vulnerabilities as and when they are released, giving you a solid edge over attackers in the fight against vulnerabilities.
Vulnerability Scanner Pc
Why does an agent-based vulnerability scanner give you an edge over agentless scanning?

Vulnerability Scanner Tools
Agents are lightweight, multipurpose tools that reside within endpoints. Since the agent resides on the client machine, it can bypass credentials and constantly keep tabs on new vulnerabilities, misconfigurations, and other security loopholes as they emerge, all without any restrictions on the scan window or any disruptions to network bandwidth.
Vulnerability Scanner Definition
Tracking assets over time in networks using dynamic IPs for network endpoints is no longer a problem since modern agents retain the vulnerability management server IP and are designed to reach out and report to the server in case of changes or disruptions. Besides, agents can replicate patch binaries directly from the server to the client machines, eliminating the need for every client machine to download patches and drastically reducing overall bandwidth consumption.