-->
- Microsoft Office Safe Mode Turn Off
- Turn Off Microsoft Office Safe Mode
- Microsoft Office Safe Mode Error
Important
The improved Microsoft 365 Defender portal is now available. This new experience brings Defender for Endpoint, Defender for Office 365, Microsoft 365 Defender, and more into the Microsoft 365 security center. Learn what's new.
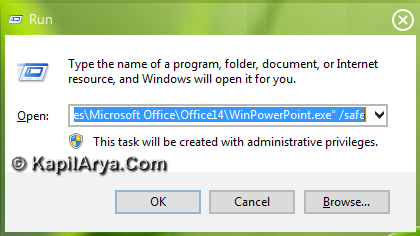
Much like Windows, Microsoft has built a Safe Mode feature into its popular productivity suite, Office. If you’re running into issues where documents crash the program after you open them, or you. Safe mode can be defined as a start-up operation mode for Operating System execution, which is also available for Windows system or the software associated with it. It is also available for the MS Outlook application and other Office suite applications.
With the new release of Microsoft Office, Microsoft has added two new safe mode settings. One is automated and fixes problems automatically. Another is manual mode, in which you have to solve MS outlook problems manually. If you are into outlook safe mode, then you have to follow some steps to get outlook out of safe mode. If you cannot open Microsoft Office program files, you can start Word, Excel, PowerPoint, Outlook, Publisher, Viso, etc, in Safe Mode in Windows 11/10. Safe mode starts Windows in a basic state, using a limited set of files and drivers. If a problem doesn't happen in safe mode, this means that default settings and basic device drivers aren't causing the issue. Observing Windows in safe mode enables you to narrow down the source of a problem, and can help you troubleshoot problems on your PC.
Applies to
Important
This article is intended for business customers who have Microsoft Defender for Office 365. If you're using Outlook.com, Microsoft 365 Family, or Microsoft 365 Personal, and you're looking for information about Safelinks in Outlook, see Advanced Outlook.com security.
Safe Links is a feature in Defender for Office 365 that provides URL scanning and rewriting of inbound email messages in mail flow, and time-of-click verification of URLs and links in email messages and other locations. Safe Links scanning occurs in addition to the regular anti-spam and anti-malware protection in inbound email messages in Exchange Online Protection (EOP). Safe Links scanning can help protect your organization from malicious links that are used in phishing and other attacks.
Safe Links protection is available in the following locations:
Email messages: Safe Links protection for links in email messages is controlled by Safe Links policies. There is no default Safe Links policy, so to get the protection of Safe Links in email messages, you need to create one or more Safe Links policies. For instructions, see Set up Safe Links policies in Microsoft Defender for Office 365.
For more information about Safe Links protection for email messages, see the Safe Links settings for email messages section later in this article.
Note
Safe Links does not work on mail-enabled public folders.
Microsoft Teams (currently in TAP Preview): Safe Links protection for links in Teams conversations, group chats, or from channels is also controlled by Safe Links policies. There is no default Safe Links policy, so to get the protection of Safe Links in Teams, you need to create one or more Safe Links policies.
For more information about Safe Links protection in Teams, see the Safe Links settings for Microsoft Teams section later in this article.
Office 365 apps: Safe Links protection for Office 365 apps is available in supported desktop, mobile, and web apps. You configure Safe Links protection for Office 365 apps in the global setting that are outside of Safe Links policies. For instructions, see Configure global settings for Safe Links settings in Microsoft Defender for Office 365.
Safe Links protection for Office 365 apps is applied to all users in the organization who are licensed for Defender for Office 365, regardless of whether the users are included in active Safe Links policies or not.
For more information about Safe Links protection in Office 365 apps, see the Safe Links settings for Office 365 apps section later in this article.
This article includes detailed descriptions of the following types of Safe Links settings:
Settings in Safe Links policies: These settings apply only to the users who are included in the specific policies, and the settings might be different between policies. These settings include:
Global Safe Links settings: These settings are configured globally, not in Safe Links policies. These settings include:
Microsoft Office Safe Mode Turn Off
The following table describes scenarios for Safe Links in Microsoft 365 and Office 365 organizations that include Defender for Office 365 (in other words, lack of licensing is never an issue in the examples).
| Scenario | Result |
|---|---|
| Jean is a member of the marketing department. Safe Links protection for Office 365 apps is turned on in the global settings for Safe Links, and a Safe Links policy that applies to members of the marketing department exists. Jean opens a PowerPoint presentation in an email message, and then clicks a URL in the presentation. | Jean is protected by Safe Links. Jean is included in a Safe Links policy, and Safe Links protection for Office 365 apps is turned on. For more information about the requirements for Safe Links protection in Office 365 apps, see the Safe Links settings for Office 365 apps section later in this article. |
| Chris's Microsoft 365 E5 organization has no Safe Links policies configured. Chris receives an email from an external sender that contains a URL to a malicious website that he ultimately clicks. | Chris is not protected by Safe Links. An admin must create at least one Safe Links policy for anyone to get Safe Links protection in inbound email messages. Chris must be included in the conditions of policy to get Safe Links protection. |
| In Pat's organization, no admins have created any Safe Links policies, but Safe Links protection for Office 365 apps is turned on. Pat opens a Word document and clicks a URL in the file. | Pat is not protected by Safe Links. Although Safe Links protection for Office 365 apps is turned on globally, Pat is not included in any active Safe Links policies, so the protection can't be applied. |
In Lee's organization, https://tailspintoys.com is configured in the Block the following URLs list in the global settings for Safe Links. A Safe Links policy that includes Lee already exists. Lee receives an email message that contains the URL https://tailspintoys.com/aboutus/trythispage. Lee clicks the URL. | The URL might be automatically blocked for Lee; it depends on the URL entry in the list and the email client Lee used. For more information, see the 'Block the following URLs' list for Safe Links section later in this article. |
| Jamie and Julia both work for contoso.com. A long time ago, admins configured Safe Links policies that apply to both of Jamie and Julia. Jamie sends an email to Julia, not knowing that the email contains a malicious URL. | Julia is protected by Safe Links if the Safe Links policy that applies to her is configured to apply to messages between internal recipients. For more information, see the Safe Links settings for email messages section later in this article. |
Safe Links settings for email messages
Safe Links scans incoming email for known malicious hyperlinks. Scanned URLs are rewritten using the Microsoft standard URL prefix: https://nam01.safelinks.protection.outlook.com. After the link is rewritten, it's analyzed for potentially malicious content.
After Safe Links rewrites a URL, the URL remains rewritten even if the message is manually forwarded or replied to (both to internal and external recipients). Additional links that are added to the forwarded or replied-to message are not rewritten. However, in the case of automatic forwarding by Inbox rules or SMTP forwarding, the URL will not be rewritten in the message that's intended for the final recipient unless that recipient is also protected by Safe Links or the URL had already been rewritten in a previous communication. Rewritten URLs apply only to HTML email, as rewriting the URL would make rich and plain text URLs unreadable, but these URLs are still scanned prior to delivery. Rich text and plain text emails containing URLs will also still be checked by a client-side API call to Safe Links at the time of click in Outlook for Desktop version 16.0.12513 or later.
The settings in Safe Links policies that apply to email messages are described in the following list:
Select the action for unknown potentially malicious URLs in messages: Enables or disables Safe Links scanning in email messages. The recommended value is On. Turning on this setting results in the following actions.
- Safe Links scanning is enabled in Outlook (C2R) on Windows.
- URLs are rewritten and users are routed through Safe Links protection when they click URLs in messages.
- When clicked, URLs are checked against a list of known malicious URLs and the 'Block the following URLs' list.
- URLs that don't have a valid reputation are detonated asynchronously in the background.
Apply real-time URL scanning for suspicious links and links that point to files: Enables real-time scanning of links, including links in email messages that point to downloadable content. The recommended value is enabled.
- Wait for URL scanning to complete before delivering the message:
- Enabled: Messages that contain URLs are held until scanning is finished. Messages are delivered only after the URLs are confirmed to be safe. This is the recommended value.
- Disabled: If URL scanning can't complete, deliver the message anyway.
- Wait for URL scanning to complete before delivering the message:
Apply Safe Links to email messages sent within the organization: Enables or disables Safe Links scanning on messages sent between internal senders and internal recipients within the same Exchange Online organization. The recommended value is enabled.
Do not track user clicks: Enables or disables storing Safe Links click data for URLs clicked in email messages. The recommend value is to leave this setting unselected (to track user clicks).
URL click tracking for links in email messages sent between internal senders and internal recipients is currently not supported.
Do not allow users to click through to original URL: Allows or blocks users from clicking through the warning page to the original URL. The recommend value is enabled.
Display the organization branding on notification and warning pages: This option shows your organization's branding on warning pages. Branding helps users identify legitimate warnings, because default Microsoft warning pages are often used by attackers. For more information about customized branding, see Customize the Microsoft 365 theme for your organization.
Do not rewrite the following URLs: Leaves URLs as they are. Keeps a custom list of safe URLs that don't need scanning. The list is unique for each Safe Links policy. For more information about the Do not rewrite the following URLs list, see the 'Do not rewrite the following URLs' lists in Safe Links policies section later in this article.
For more information about the recommended values for Standard and Strict policy settings for Safe Links policies, see Safe Links policy settings.
Recipient filters: You need to specify the recipient conditions and exceptions that determine who the policy applies to. You can use these properties for conditions and exceptions:
- The recipient is
- The recipient domain is
- The recipient is a member of
You can only use a condition or exception once, but the condition or exception can contain multiple values. Multiple values of the same condition or exception use OR logic (for example, <recipient1> or <recipient2>). Different conditions or exceptions use AND logic (for example, <recipient1> and <member of group 1>).
Priority: If you create multiple policies, you can specify the order that they're applied. No two policies can have the same priority, and policy processing stops after the first policy is applied.
For more information about the order of precedence and how multiple policies are evaluated and applied, see Order and precedence of email protection.
How Safe Links works in email messages
At a high level, here's how Safe Links protection works on URLs in email messages:
All email goes through EOP, where internet protocol (IP) and envelope filters, signature-based malware protection, anti-spam and anti-malware filters before the message is delivered to the recipient's mailbox.
The user opens the message in their mailbox and clicks on a URL in the message.
Safe Links immediately checks the URL before opening the website:
If the URL is included in the Block the following URLs list, a blocked URL warning opens.
If the URL points to a website that has been determined to be malicious, a malicious website warning page (or a different warning page) opens.
If the URL points to a downloadable file, and the Apply real-time URL scanning for suspicious links and links that point to files setting is enabled in the policy that applies to the user, the downloadable file is checked.
If the URL is determined to be safe, the website opens.
Safe Links settings for Microsoft Teams
You enable or disable Safe Links protection for Microsoft Teams in Safe Links policies. Specifically, you use the Select the action for unknown or potentially malicious URLs within Microsoft Teams setting. The recommended value is On.
The following settings in Safe Links policies that apply to links in email messages also apply to links in Teams:
- Apply real-time URL scanning for suspicious links and links that point to files
- Do not track user clicks
- Do not allow users to click through to original URL
These settings are explained previously in Safe Links settings for email messages.
After you turn on Safe Links protection for Microsoft Teams, URLs in Teams are checked against a list of known malicious links when the protected user clicks the link (time-of-click protection). URLs are not rewritten. If a link is found to be malicious, users will have the following experiences:
- If the link was clicked in a Teams conversation, group chat, or from channels, the warning page as shown in the screenshot below will appear in the default web browser.
- If the link was clicked from a pinned tab, the warning page will appear in the Teams interface within that tab. The option to open the link in a web browser is disabled for security reasons.
- Depending on how the Do not allow users to click through to original URL setting in the policy is configured, the user will or will not be allowed to click through to the original URL (Continue anyway (not recommended) in the screenshot). We recommend that you enable the Do not allow users to click through to original URL setting so users can't click through to the original URL.
If the user who sent the link isn't included in a Safe Links policy where Teams protection is enabled, the user is free to click through to the original URL on their computer or device.
Clicking the Go Back button on the warning page will return the user to their original context or URL location. However, clicking on the original link again will cause Safe Links to rescan the URL, so the warning page will reappear.
How Safe Links works in Teams
At a high level, here's how Safe Links protection works for URLs in Microsoft Teams:
A user starts the Teams app.
Microsoft 365 verifies that the user's organization includes Microsoft Defender for Office 365, and that the user is included in an active Safe Links policy where protection for Microsoft Teams is enabled.
URLs are validated at the time of click for the user in chats, group chats, channels, and tabs.
Safe Links settings for Office 365 apps
Safe Links protection for Office 365 apps checks links in Office documents, not links in email messages (but it can check links in attached Office documents in email messages after the document is opened).
Safe Links protection for Office 365 apps has the following client requirements:
Microsoft 365 Apps or Microsoft 365 Business Premium.
- Current versions of Word, Excel, and PowerPoint on Windows, Mac, or in a web browser.
- Office apps on iOS or Android devices.
- Visio on Windows.
- OneNote in a web browser.
Office 365 apps are configured to use modern authentication. For more information, see How modern authentication works for Office 2013, Office 2016, and Office 2019 client apps.
Users are signed in using their work or school accounts. For more information, see Sign in to Office.
You configure Safe Links protection for Office 365 apps in the global settings for Safe Links, not in Safe Links policies. The protection is applied to all users in the organization who are licensed for Defender for Office 365, regardless of whether the users are included in active Safe Links policies or not.
The following Safe Links settings are available for Office 365 apps:
Office 365 applications: Enables or disables Safe Links scanning in supported Office 365 apps. The default and recommended value is On.
Do not track when users click Safe Links: Enables or disables storing Safe Links click data for URLs clicked in the desktop versions Word, Excel, PowerPoint, and Visio. The recommended value is Off, which means user clicks are tracked.
Do not let users click through safe links to original URL: Allows or blocks users from clicking through the warning page to the original URL in in the desktop versions Word, Excel, PowerPoint, and Visio. The default and recommended value is On.
To configure the Safe Links settings for Office 365 apps, see Configure Safe Links protection for Office 365 apps.
For more information about the recommended values for Standard and Strict policy settings, see Global settings for Safe Links.
How Safe Links works in Office 365 apps
At a high level, here's how Safe Links protection works for URLs in Office 365 apps. The supported Office 365 apps are described in the previous section.
A user signs in using their work or school account in an organization that includes Microsoft 365 Apps or Microsoft 365 Business Premium.
The user opens and clicks on a link an Office document in a supported Office app.
Safe Links immediately checks the URL before opening the target website:
If the URL is included in the list that skips Safe Links scanning (the Block the following URLs list) a blocked URL warning page opens.
If the URL points to a website that has been determined to be malicious, a malicious website warning page (or a different warning page) opens.
If the URL points to a downloadable file, and the Safe Links policy that applies to the user is configured to scan links to downloadable content (Apply real-time URL scanning for suspicious links and links that point to files), the downloadable file is checked.
If the URL is considered safe, the user is taken to the website.
If Safe Links scanning is unable to complete, Safe Links protection does not trigger. In Office desktop clients, the user will be warned before they proceed to the destination website.
Note
It may take several seconds at the beginning of each session to verify that the user has Safe Links for Office enabled.
'Block the following URLs' list for Safe Links
The Block the following URLs list defines the links that are always blocked by Safe Links scanning in the following locations:
- Email messages.
- Documents in Office 365 apps in Windows and Mac.
- Documents in Office for iOS and Android.
When a user in an active Safe Links policy clicks a blocked link in a supported app, they're taken to the Blocked URL warning page.
You configure the list of URLs in the global settings for Safe Links. For instructions, see Configure the 'Block the following URLs' list.
Notes:
- For a truly universal list of URLs that are blocked everywhere, see Manage the Tenant Allow/Block List.
- Limits for the Block the following URLs list:
- The maximum number of entries is 500.
- The maximum length of an entry is 128 characters.
- All of the entries can't exceed 10,000 characters.
- Don't include a forward slash (
/) at the end of the URL. For example, usehttps://www.contoso.com, nothttps://www.contoso.com/. - A domain only-URL (for example
contoso.comortailspintoys.com) will block any URL that contains the domain. - You can block a subdomain without blocking the full domain. For example,
toys.contoso.com*blocks any URL that contains the subdomain, but it doesn't block URLs that contain the full domaincontoso.com. - You can include up to three wildcards (
*) per URL entry.
Turn Off Microsoft Office Safe Mode
Entry syntax for the 'Block the following URLs' list
Examples of the values that you can enter and their results are described in the following table:
| Value | Result |
|---|---|
contoso.comor
| Blocks the domain, subdomains, and paths. For example, https://www.contoso.com, https://sub.contoso.com, and https://contoso.com/abc are blocked. |
https://contoso.com/a | Blocks https://contoso.com/a but not additional subpaths like https://contoso.com/a/b. |
https://contoso.com/a* | Blocks https://contoso.com/a and additional subpaths like https://contoso.com/a/b. |
https://toys.contoso.com* | Blocks a subdomain (toys in this example) but allow clicks to other domain URLs (like https://contoso.com or https://home.contoso.com). |
'Do not rewrite the following URLs' lists in Safe Links policies
Note
If your organization use Safe Links policies, the Do not rewrite the following URLs lists are the only supported method for third party phishing tests.
Each Safe Links policy contains a Do not rewrite the following URLs list that you can use to specify URLs that are not rewritten by Safe Links scanning. In other words, the list allows users who are included in the policy to access the specified URLs that would otherwise be blocked by Safe Links. You can configure different lists in different Safe Links policies. Policy processing stops after the first (likely, the highest priority) policy is applied to the user. So, only one Do not rewrite the following URLs list is applied to a user who is included in multiple active Safe Links policies.
To add entries to the list in new or existing Safe Links policies, see Create Safe Links policies or Modify Safe Links policies.
Notes:
The following clients don't recognize the Do not rewrite the following URLs lists in Safe Links policies. Users included in the polices can be blocked from accessing the URLs based on the results of Safe Links scanning in these clients:
- Microsoft Teams
- Office web apps
For a truly universal list of URLs that are allowed everywhere, see Manage the Tenant Allow/Block List.
Consider adding commonly used internal URLs to the list to improve the user experience. For example, if you have on-premises services, such as Skype for Business or SharePoint, you can add those URLs to exclude them from scanning.
If you already have Do not rewrite the following URLs entries in your Safe Links policies, be sure to review the lists and add wildcards as required. For example, your list has an entry like
https://contoso.com/aand you later decide to include subpaths likehttps://contoso.com/a/b. Instead of adding a new entry, add a wildcard to the existing entry so it becomeshttps://contoso.com/a/*.You can include up to three wildcards (
*) per URL entry. Wildcards explicitly include prefixes or subdomains. For example, the entrycontoso.comis not the same as*.contoso.com/*, because*.contoso.com/*allows people to visit subdomains and paths in the specified domain.If a URL uses automatic redirection for HTTP to HTTPS (for example, 302 redirection for
http://www.contoso.comtohttps://www.contoso.com), and you try to enter both HTTP and HTTPS entries for the same URL to the list, you might notice that the second URL entry replaces the first URL entry. This behavior does not occur if the HTTP and HTTPS versions of the URL are completely separate.
Entry syntax for the 'Do not rewrite the following URLs' list
Examples of the values that you can enter and their results are described in the following table:
| Value | Result |
|---|---|
contoso.com | Allows access to https://contoso.com but not subdomains or paths. |
*.contoso.com/* | Allows access to a domain, subdomains, and paths (for example, https://www.contoso.com, https://www.contoso.com, https://maps.contoso.com, or https://www.contoso.com/a). This entry is inherently better than |
https://contoso.com/a | Allows access to https://contoso.com/a, but not subpaths like https://contoso.com/a/b |
https://contoso.com/a/* | Allows access to https://contoso.com/a and subpaths like https://contoso.com/a/b |
Warning pages from Safe Links
This section contains examples of the various warning pages that are triggered by Safe Links protection when you click a URL.
Note that several warning pages have been updated. If you're not already seeing the updated pages, you will soon. The updated pages include a new color scheme, more detail, and the ability to proceed to a site despite the given warning and recommendations.
Scan in progress notification
The clicked URL is being scanned by Safe Links. You might need to wait a few moments before trying the link again.
The original notification page looked like this:
Suspicious message warning
The clicked URL was in an email message that's similar to other suspicious messages. We recommend that you double-check the email message before proceeding to the site.
Phishing attempt warning
The clicked URL was in an email message that has been identified as a phishing attack. As a result, all URLs in the email message are blocked. We recommend that you do not proceed to the site.
Malicious website warning
The clicked URL points to a site that has been identified as malicious. We recommend that you do not proceed to the site.
The original warning page looked like this:
Blocked URL warning
The clicked URL has been manually blocked by an admin in your organization (the Block the following URLs list in the global settings for Safe Links). The link was not scanned by Safe Links because it was manually blocked.
There are several reasons why an admin would manually block specific URLs. If you think the site should not be blocked, contact your admin.
The original warning page looked like this:
Error warning
Some kind of error has occurred, and the URL can't be opened.
The original warning page looked like this:
-->Original KB number: 3140179
Symptoms
When you try to open an Office 2016 or Office 2013 application, such as Outlook, Word, Excel, PowerPoint, OneNote, or Access, one of the following errors may be displayed, depending on the installation type of Office.
Microsoft Office Safe Mode Error
Click-to-Run installation type:
Something went wrongWe couldn't start your program. Please try starting it again.If it won't start, try repairing Office from 'Programs and Features' in the Control Panel.
MSI-based installation type:
Microsoft Office can't find your license for this application. A repair attempt was unsuccessful or was cancelled. Microsoft Office will now exit.
Cause
This issue occurs when you try to start an Office 2016 or Office 2013 application while Microsoft Windows is running in safe mode.
Workaround
To work around this issue, start Windows by using the Selective Startup option in System Configuration instead of safe mode. The steps to configure Selective Startup vary, depending on your Office installation type.
Click-to-Run installation type:
Open System Configuration. To do this, press the Windows Key + R to open a Run dialog box. Type msconfig, and then click OK.
Select Selective startup, and then clear the Load system services and Load startup items check boxes.
Click the Services tab.
Select the Microsoft Office ClickToRun Service check box.
Click OK.
If you're prompted, click Restart.
MSI-based installation type:
Open System Configuration. To do this, press the Windows Key + R to open a Run dialog box. Type msconfig, and then click OK.
Select Selective startup, and then clear the Load system services and Load startup items check boxes.
Click OK.
If you're prompted, click Restart.
When you have finished troubleshooting and no longer need to run in Selective startup, return to Normal startup by following these steps:
- Open System Configuration. To do this, press the Windows Key + R to open a Run dialog box. Type msconfig, and then click OK.
- Select Normal startup.
- Click OK.
- If you're prompted, click Restart.
More information

To determine whether your Office installation is Click-to-Run or MSI-based, follow these steps:
Start an Office application, such as Outlook or Word.
On the File menu, select Account or Office Account.
For Office Click-to-Run installations, an Update Options item is displayed. For MSI-based installations, the Update Options item isn't displayed.
Click-to-Run Office installation MSI-based Office installation